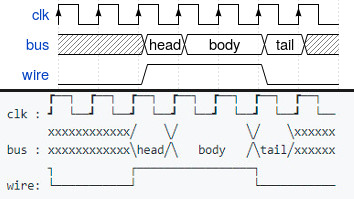
I found this json text in a .srt file for a video [closed]
So i am not sure what does this actually do i understand that its a get request but that’s how far my knowledge is
{
"threads":[{"position":24444914,"start":0,"end":25606282,"connection":&q… Continue reading I found this json text in a .srt file for a video [closed]