JavaScript Best Practices
Learn about the best practices for web development and JavaScript programming, complete with code examples and real-world scenarios. Continue reading JavaScript Best Practices
Collaborate Disseminate
Learn about the best practices for web development and JavaScript programming, complete with code examples and real-world scenarios. Continue reading JavaScript Best Practices
When I see examples of CSRF attacks, it is almost always explained with someone entering some external API url in an <img> tag, e.g. <img src="bank.com/transfer?amount=10000?recipient=badguy">. Or it involves a form w… Continue reading Why do most examples of CSRF use roundabout ways of executing an API call instead of just using pure Javascript?
Have some confusion regarding safe sinks in javascript.
The DOMpurify library linked in the OWASP article does not explicitly mention the .files and .valueAsDate of an HTMLInputElement as safe sinks, but the more common .value is a safe si… Continue reading Safe Sinks js confusion
I want to put a router link to another subsite to my code. For example when I want to log in, it should redirect me to the login page.
Is that secure and is there any lack of data or space for data-loss?
Continue reading How can I put a router link in my javascript? [closed]
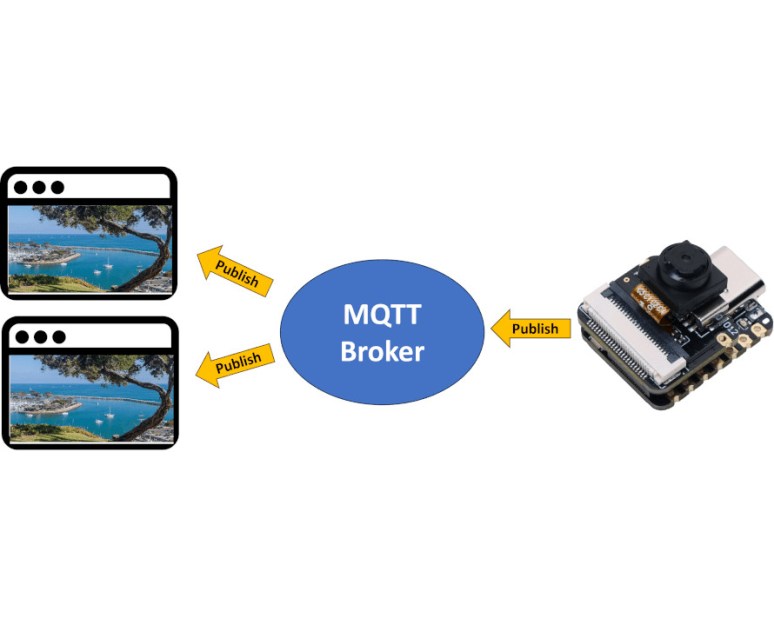
The ESP32, while first thought to be little more than a way of adding wireless capabilities to other microcontrollers, has quickly replaced many of them with its ability to be …read more Continue reading Streaming Video From an ESP32
Can one remotely log my IP, browser history, and saved passwords?
I think the IP should be easily done if one of the extensions load a remote JavaScript to run in my browser. I’m not sure about other stuff within the browser.
By Owais Sultan
At its core, web scraping involves automatically extracting data from websites, enabling individuals and organizations to obtain valuable…
This is a post from HackRead.com Read the original post: Overcoming web scraping blocks: Be… Continue reading Overcoming web scraping blocks: Best practices and considerations
With security schema, Splunk and collaborators aim to transform alert telemetry from cacophony to chorus with one taxonomy across vendors and tools. Continue reading At Black Hat, Splunk, AWS, IBM Security and Others Launch Open Source Cybersecurity Framework
I am studying cybersecurity and I am trying to make sure that I will study all the basics
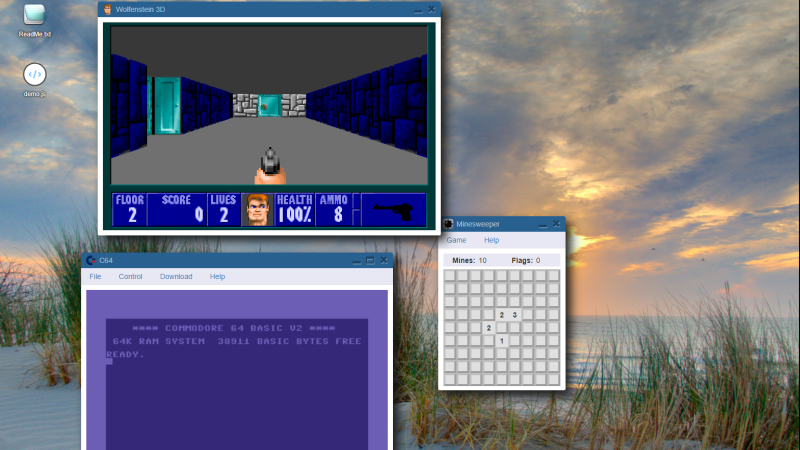
[Hugo Leisink] is a programmer who contributes to Open Source projects. In their spare time, they have been developing a web-browser-based operating system called Orb. It is available for the …read more Continue reading The Orb Web Desktop