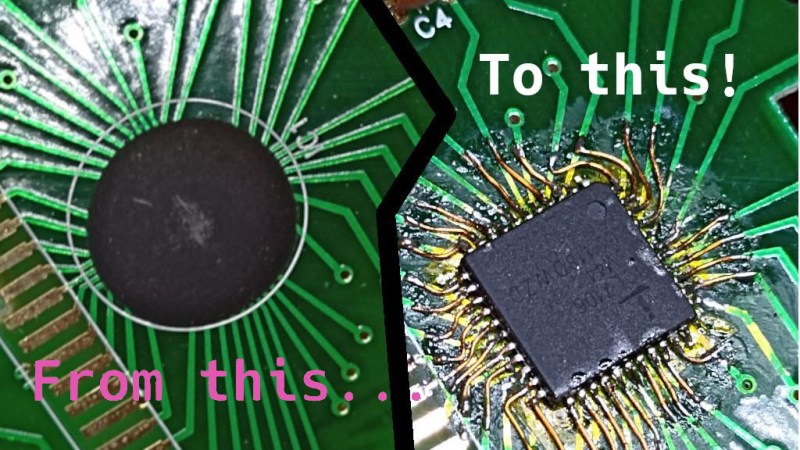
Surface Mount Soldering Practice for Budding Electrical Engineers

Electronics components are steadily moving away from through hole parts to using surface mount technology (SMT) exclusively. While the small size of the SMT components can be intimidating, with a …read more Continue reading Surface Mount Soldering Practice for Budding Electrical Engineers