Smart Sphere or Magnetic Magic

Sometimes a coworker sees something on your desk, and they have to ask, “Where can I get one of those?” and that has to be one of the greatest compliments …read more Continue reading Smart Sphere or Magnetic Magic
Collaborate Disseminate

Sometimes a coworker sees something on your desk, and they have to ask, “Where can I get one of those?” and that has to be one of the greatest compliments …read more Continue reading Smart Sphere or Magnetic Magic
In this Help Net Security video, Nick Mistry, SVP and CISO at Lineaje, offers tips to simplify the process of compliance with U.S. Executive Order 14028. A key part of U.S. Executive Order 14028 is for organizations that work with federal agencies to p… Continue reading How to simplify the process of compliance with U.S. Executive Order 14028
Organizations that closely align their cybersecurity programs to business objectives are 18% more likely to achieve target revenue growth and market share and improve customer satisfaction, as well as 26% more likely to lower the cost of cybersecurity … Continue reading Three cybersecurity actions that make a difference
With the rise of modern trends such as cloud computing and remote work, healthcare institutions strive to balance accessibility, convenience, and robust security. In this Help Net Security interview, Ken Briggs, General Counsel at Salucro, discusses ho… Continue reading Building a culture of security awareness in healthcare begins with leadership
In this Help Net Security video interview, Rick Howard, CSO of N2K, Chief Analyst, and Senior Fellow at the Cyberwire, discusses his book – Cybersecurity First Principles: A Reboot of Strategy and Tactics. In the book, Howard challenges the conve… Continue reading Introducing the book: Cybersecurity First Principles
In this Help Net Security video, Jason Lewkowicz, Chief Services Officer at Optiv, discusses mental health in cybersecurity, which needs more attention. There is a confluence of factors – from the cybersecurity talent shortage and reductions in force t… Continue reading Managing mental health in cybersecurity
Building a custom cracking rig for research can be expensive, so penetration tester Max Ahartz built one on AWS. In this Help Net Security interview, he takes us through the process and unveils the details of his creation. What motivated you to underta… Continue reading Penetration tester develops AWS-based automated cracking rig
By Owais Sultan
In the current high-tech age, consumer data is a business’s most important asset as they progressively shifts towards…
This is a post from HackRead.com Read the original post: Adobe Real-Time CDP: Personalized Customer Exper… Continue reading Adobe Real-Time CDP: Personalized Customer Experience
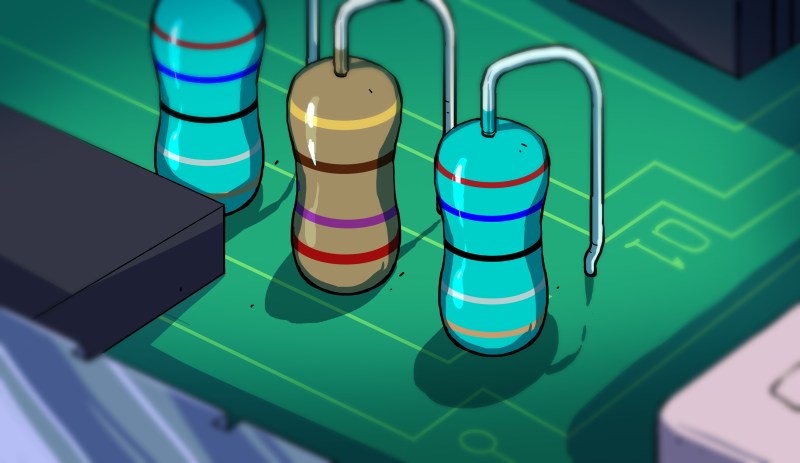
When it comes to things that hackers build, PCBs are a sizeable portion of our creative output. It’s no wonder – PCB design is a powerful way to participate in …read more Continue reading Share Your Projects: Making Helpful PCBs
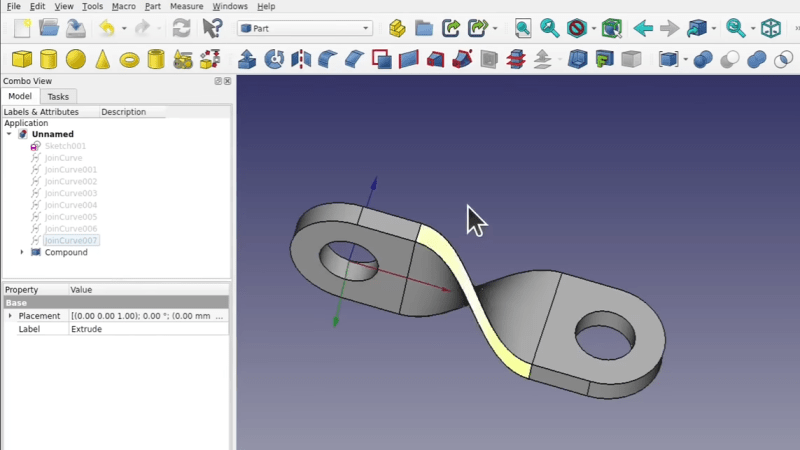
Quick references are handy, but sometimes it’s nice to have a process demonstrated from beginning to end. In that spirit, [Darren Stone] created a video demonstrating how to model a …read more Continue reading How To Model a Twisted Part in FreeCAD