This file is supposed to help with finding a solution for a memory dump but it is encrypted. what encryption is it? [closed]
This file does not have a file extension. It is just labelled "data".
Collaborate Disseminate
This file does not have a file extension. It is just labelled "data".

Seeing the unseen is one of the great things about using an infrared (IR) camera, and even the cheap-ish ones that plug into a smartphone can dramatically improve your hardware …read more Continue reading Lock-In Thermography on a Cheap IR Camera
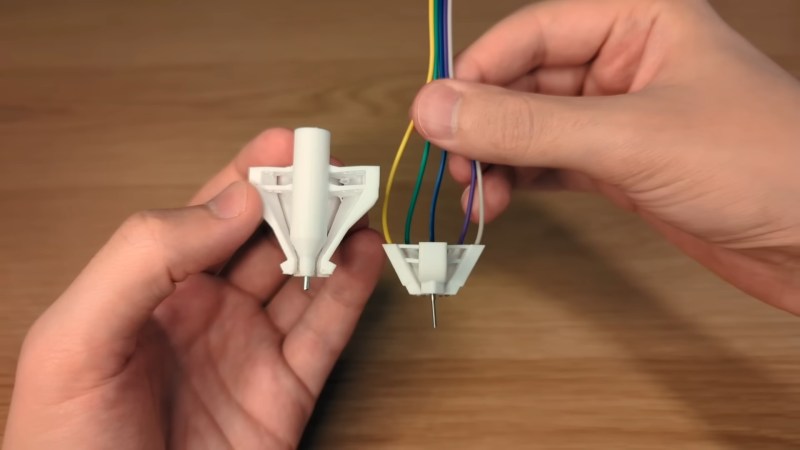
The proliferation of microcontrollers has made it easier than ever to add some smarts to a project, but sometimes there just isn’t enough space for headers on a board, or …read more Continue reading SWD Interface Simplifies Debugging
I was trying to overflow the return pointer of a simple program. I have asrl disabled and I compiled like this gcc returnexp.c -o returnexp -fno-stack-protector.
(I would disable noexecstack later on when I could overwrite the pointer)
Bu… Continue reading Segmentation fault without rip even getting overwritten Buffer Overflow
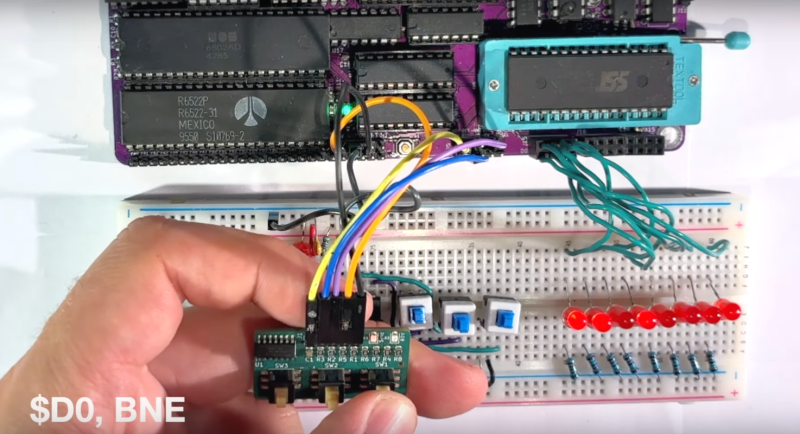
Although marketing folk and laypeople may credit [Steve Jobs] as the man behind the success of Apple, those in the tech world know the real truth that without [Steve Wozniak] …read more Continue reading Single-Stepping the 6502 Processor
There are JavaScript libraries (such as dev-tools-monitor, devtools-detector, devtools-detect and others) that detect when the developer console is open. Are there also ways to better hide the dev-tools such that they are no longer detecta… Continue reading How to use the web developer console when sites detect its use? [migrated]
When I try to perform a DLL injection with ScyllaHide in x32/x64 dbg, then it crashes for some reason, is this a bug? Both with stealthy injection as with normal injection, the program crashes when I inject a DLL.
For example, when I injec… Continue reading ScyllaHide DLL Injection
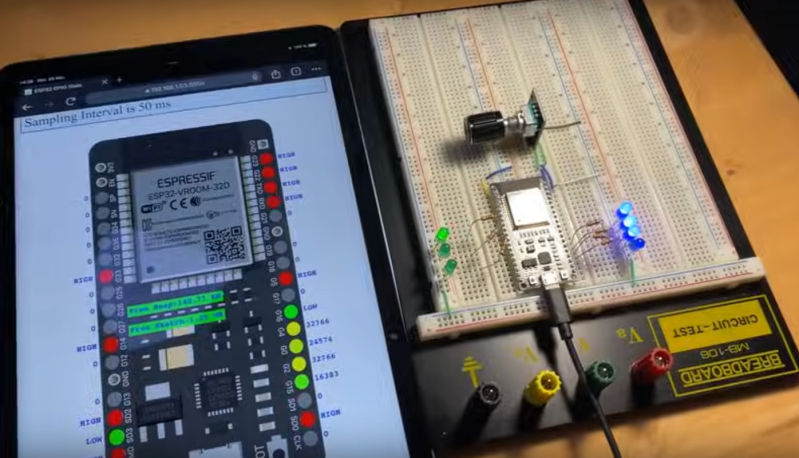
The ESP32 has been a go-to microcontroller platform for a while now, thanks to its versatile capabilities, integrated Wi-Fi and Bluetooth connectivity, and low power consumption. It’s ideal for a …read more Continue reading Spying on the ESP32’s GPIO
I can imagine this is a difficult question for you to answer without seeing the actual sample, but perhaps some of you have experience with this. I’m analysing a sample from Darkside using IDA Free and x32dbg and I have resolved the dynami… Continue reading Ransomware debugging Imports Scylla
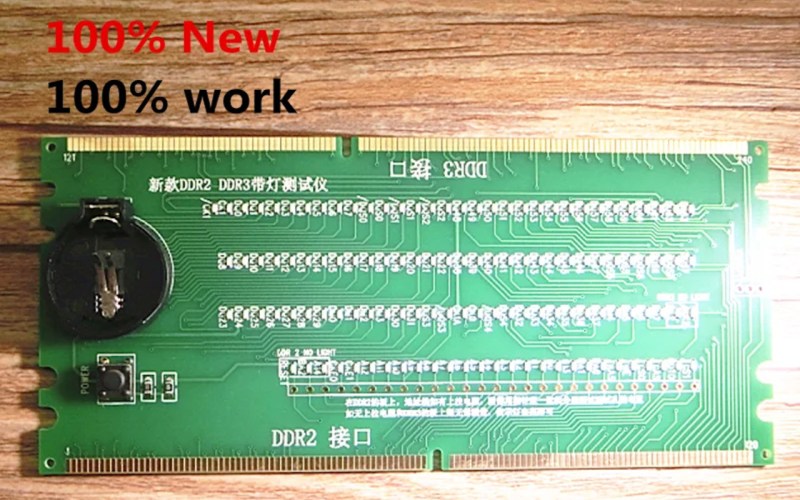
Humans are walking high voltage generators, due to all the friction with our surroundings, wide variety of synthetic clothes, and the overall everpresent static charges. Our electronics are sensitive to …read more Continue reading Hacker Tactic: Internal ESD Diode Probing