March 2025 Web Server Survey
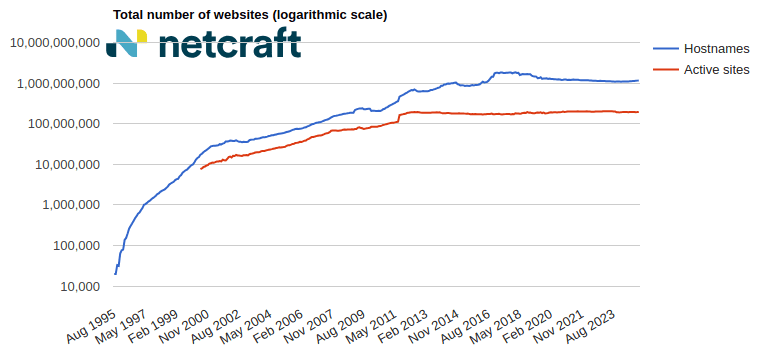
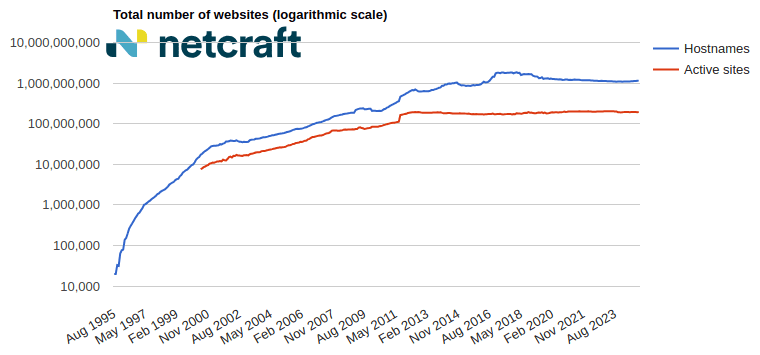
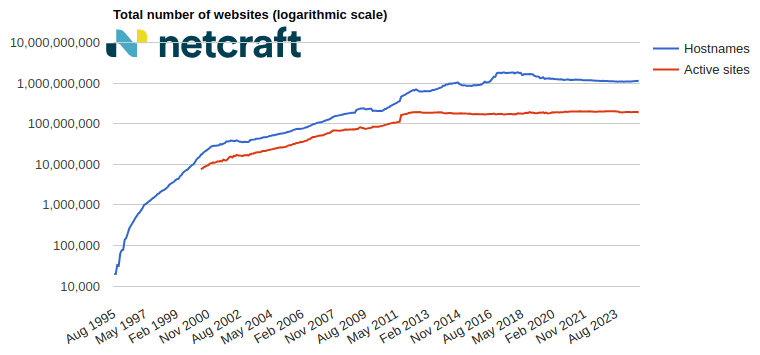
In the March 2025 survey we received responses from 1,197,680,522 sites across 275,633,322 domains and 13,402,722 web-facing computers. This reflects an increase of 17.0 million sites and 976,381 domains, and a loss of 77,628 web-facing computers.
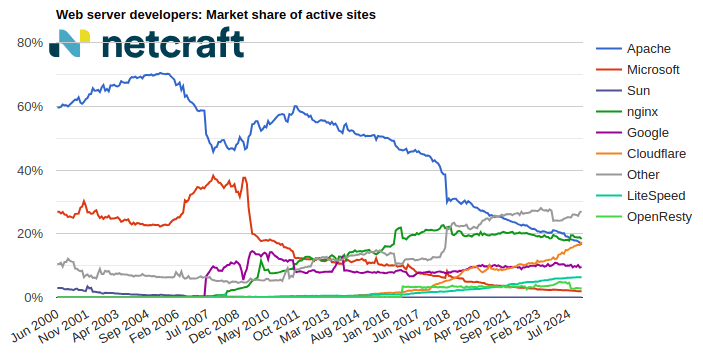
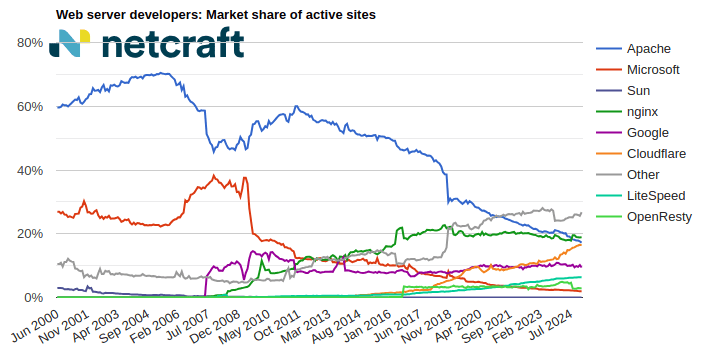
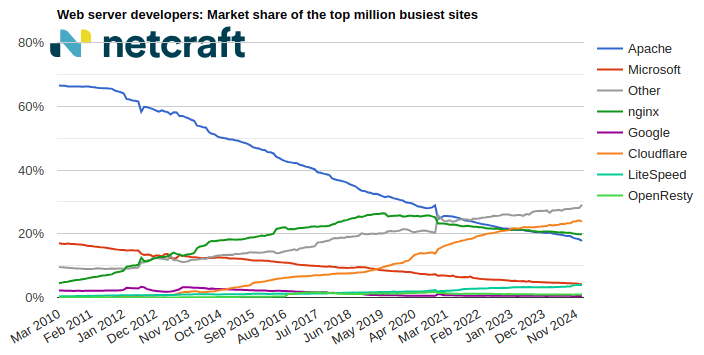
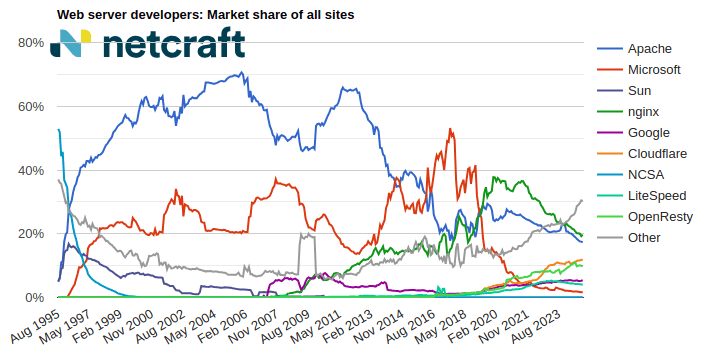
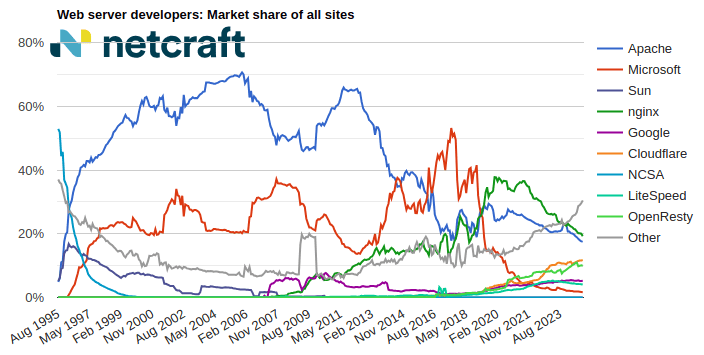
nginx made the largest gain of 5.1 million sites (+2.12%) this month, increasing its market share to 20.5% (+0.14pp). Cloudflare made the next largest gain of 3.7 million sites (+2.49%).
Apache suffered the largest loss of 451,949 sites (-0.23%) this month, and now accounts for 16.0% (-0.27pp) of sites seen by Netcraft. Microsoft experienced the next largest loss of 189,378 sites (-1.03%).
Vendor news
- Google Cloud launched a new region in Sweden on March 6th.
- Apache Tomcat versions 9.0.102, 10.1.39 and 11.05 were released between March 5th and 7th. These versions improve protection against a race condition allowing remote code execution on case insensitive filesystems.
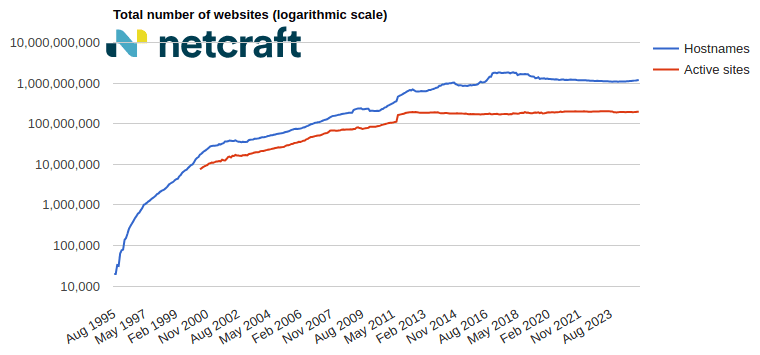
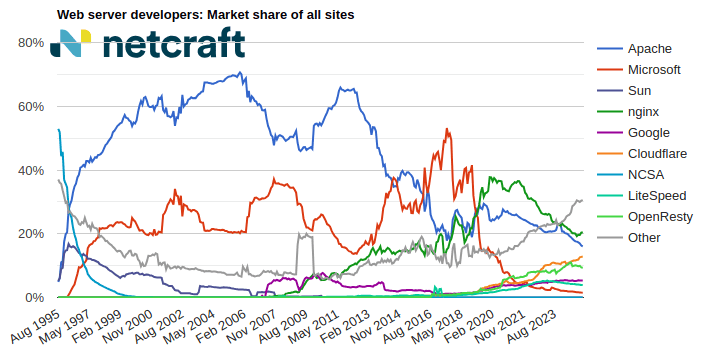
| Developer | February 2025 | Percent | March 2025 | Percent | Change |
|---|---|---|---|---|---|
| nginx | 240,182,690 | 20.34% | 245,275,749 | 20.48% | 0.14 |
| Apache | 192,401,922 | 16.30% | 191,949,973 | 16.03% | -0.27 |
| Cloudflare | 150,432,756 | 12.74% | 154,171,314 | 12.87% | 0.13 |
| OpenResty | 111,442,093 | 9.44% | 112,063,651 | 9.36% | -0.08 |
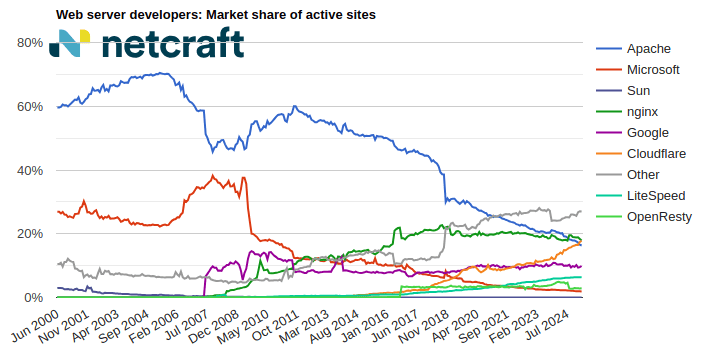
| Developer | February 2025 | Percent | March 2025 | Percent | Change |
|---|---|---|---|---|---|
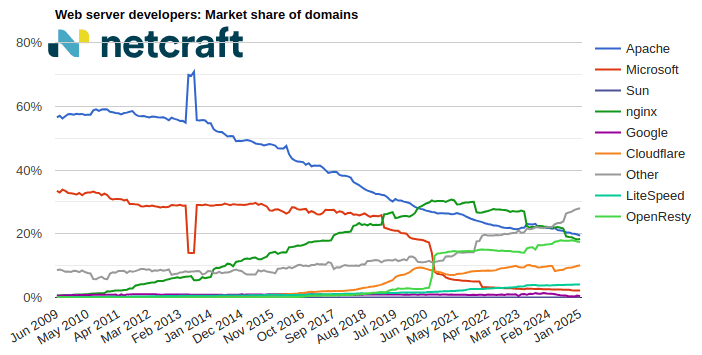
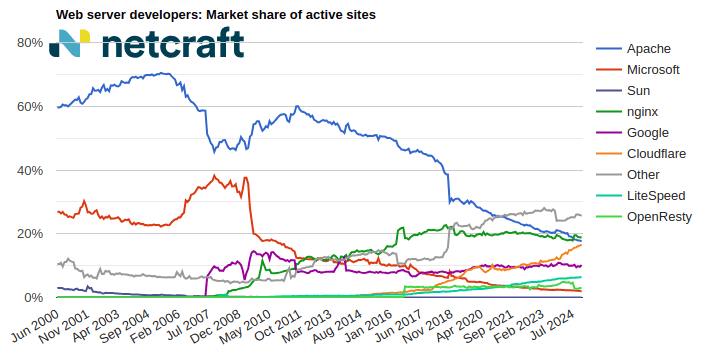
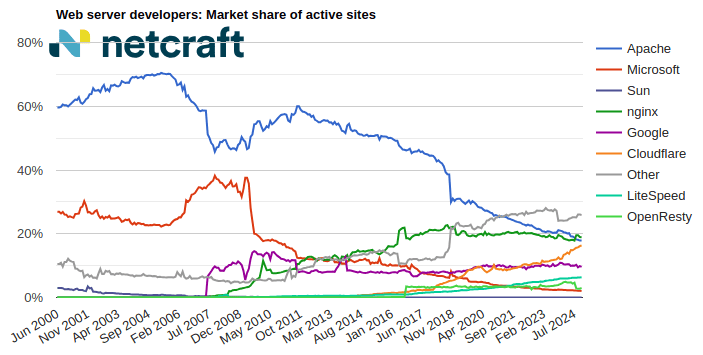
| nginx | 36,179,069 | 18.38% | 35,283,083 | 17.89% | -0.49 |
| Cloudflare | 34,245,606 | 17.40% | 35,122,370 | 17.81% | 0.41 |
| Apache | 32,549,711 | 16.54% | 32,140,051 | 16.30% | -0.24 |
| 18,744,996 | 9.52% | 19,492,434 | 9.89% | 0.36 |
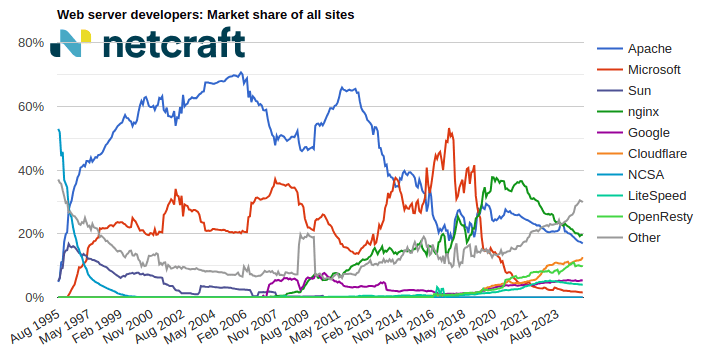
For more information see Active Sites.
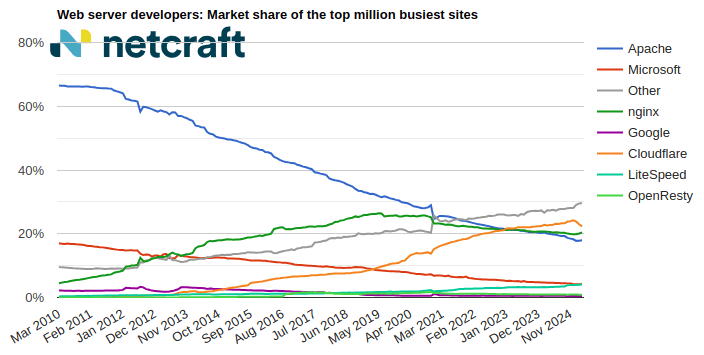
| Developer | February 2025 | Percent | March 2025 | Percent | Change |
|---|---|---|---|---|---|
| Cloudflare | 229,874 | 22.99% | 223,176 | 22.32% | -0.67 |
| nginx | 201,058 | 20.11% | 203,732 | 20.37% | 0.27 |
| Apache | 178,287 | 17.83% | 179,491 | 17.95% | 0.12 |
| Microsoft | 41,612 | 4.16% | 42,049 | 4.20% | 0.04 |
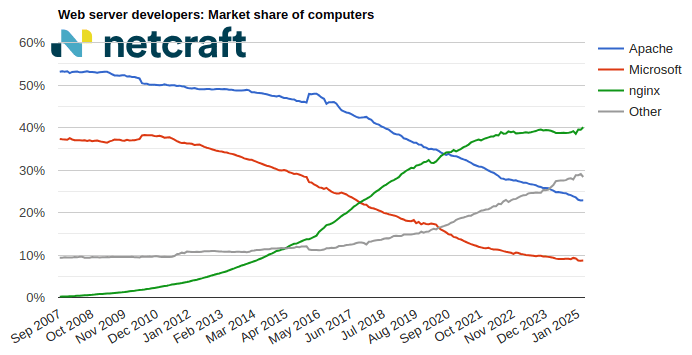
| Developer | February 2025 | Percent | March 2025 | Percent | Change |
|---|---|---|---|---|---|
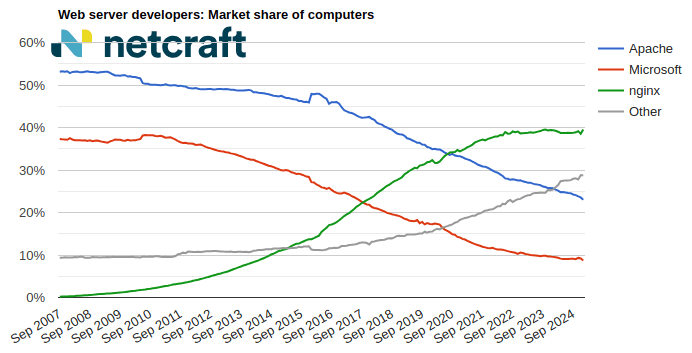
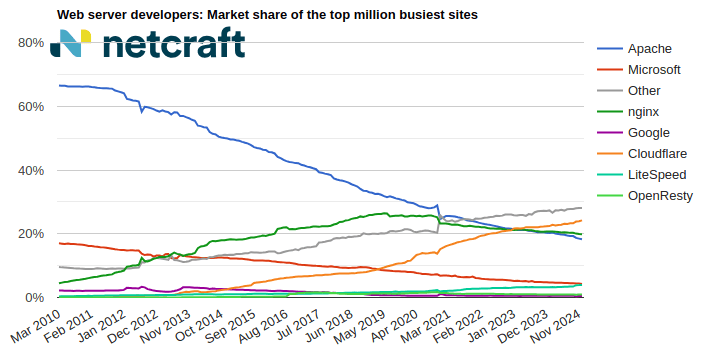
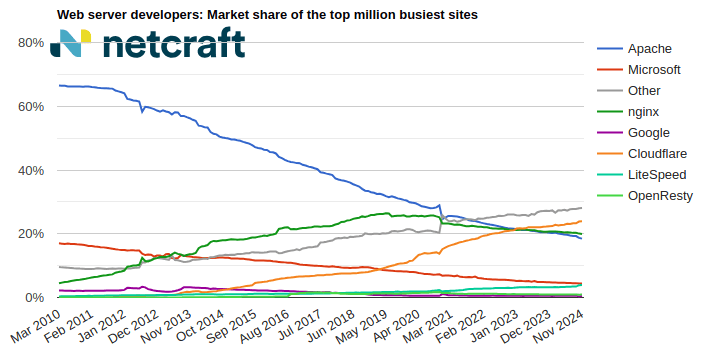
| nginx | 5,319,894 | 39.46% | 5,368,409 | 40.05% | 0.59 |
| Apache | 3,079,017 | 22.84% | 3,066,454 | 22.88% | 0.04 |
| Microsoft | 1,166,631 | 8.65% | 1,166,997 | 8.71% | 0.05 |
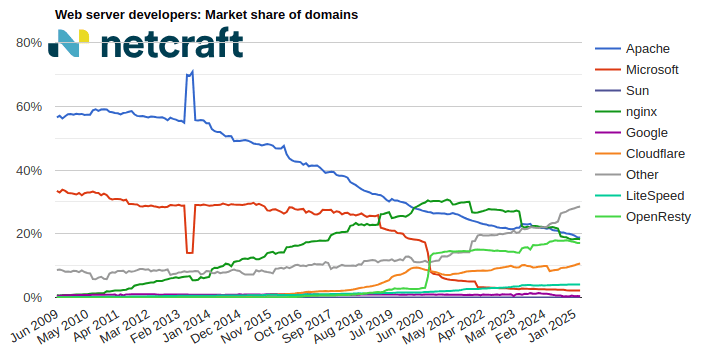
| Developer | February 2025 | Percent | March 2025 | Percent | Change |
|---|---|---|---|---|---|
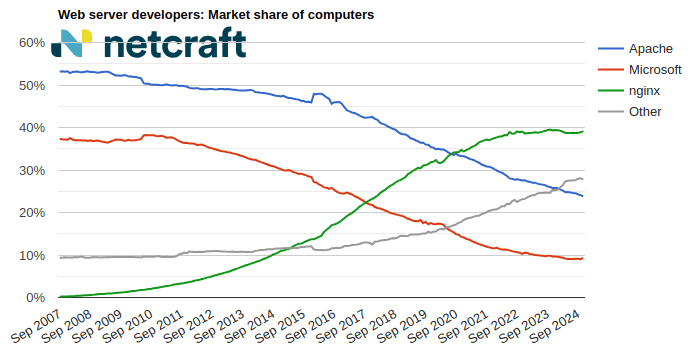
| Apache | 51,860,896 | 18.88% | 51,840,052 | 18.81% | -0.07 |
| nginx | 50,684,106 | 18.45% | 50,292,713 | 18.25% | -0.21 |
| OpenResty | 47,057,779 | 17.13% | 47,174,160 | 17.11% | -0.02 |
| Cloudflare | 28,694,732 | 10.45% | 29,368,444 |