Forget Pixel Art: Try Subpixels
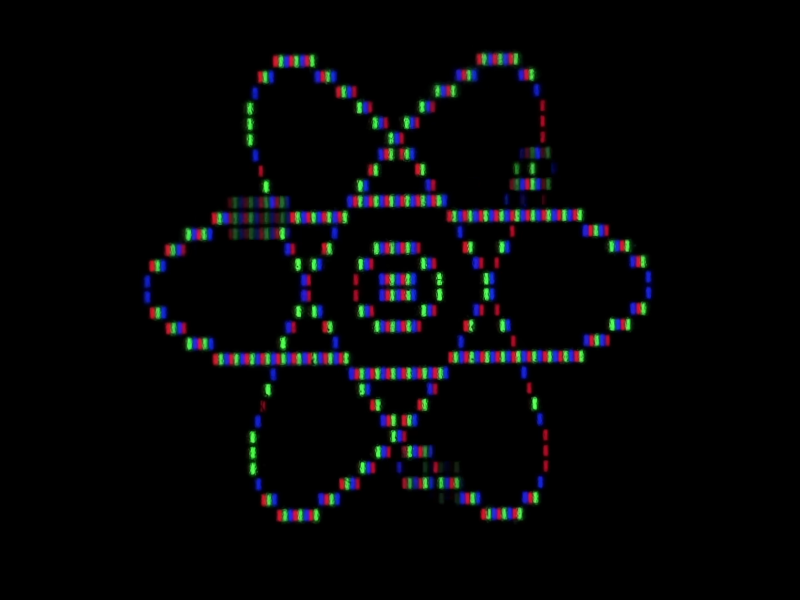
[Japhy Riddle] was tired of creating pixel art. He went to subpixel art. The idea is that since each color pixel is composed of three subpixels, your display is actually …read more Continue reading Forget Pixel Art: Try Subpixels