Homemade VNA Delivers High-Frequency Performance on a Budget
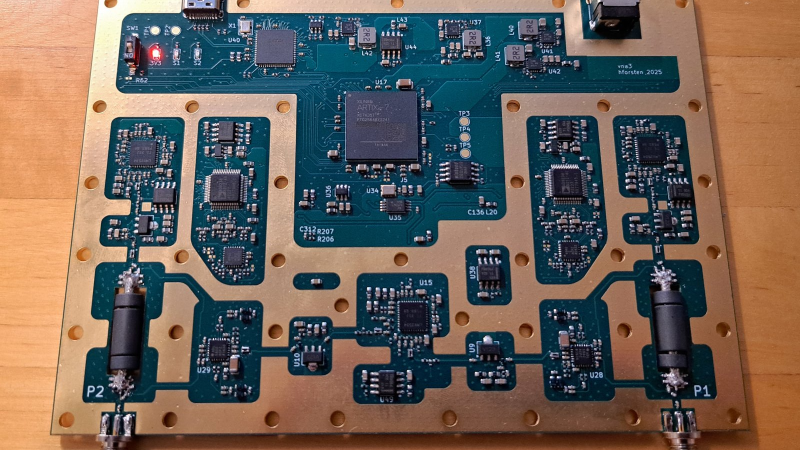
With vector network analyzers, the commercial offerings seem to come in two flavors: relatively inexpensive but limited capabilities, and full-featured but scary expensive. There doesn’t seem to be much middle …read more Continue reading Homemade VNA Delivers High-Frequency Performance on a Budget