
Enlarge / Damn computer hackers, always trying to steal all my stuff. (credit: Getty Images / C.J. Burton)
This article was originally published on Scott Helme’s blog and is reprinted here with his permission.
We have a little problem on the web right now and I can only see it becoming a larger concern as time goes by: more and more sites are obtaining certificates, vitally important documents needed to deploy HTTPS, but we have no way of protecting ourselves when things go wrong.
Certificates
We’re currently seeing a bit of a gold rush for certificates on the Web as more and more sites deploy HTTPS. Beyond the obvious security and privacy benefits of HTTPS, there are quite a few reasons you might want to consider moving to a secure connection that I outline in my article Still think you don’t need HTTPS?. Commonly referred to as “SSL certificates” or “HTTPS certificates”, the wider Internet is obtaining them at a rate we’ve never seen before in the history of the web. Every day I crawl the top one million sites on the Web and analyze various aspects of their security and every 6 months I publish a report. You can see the reports here, but the main result to focus on right now is the adoption of HTTPS.
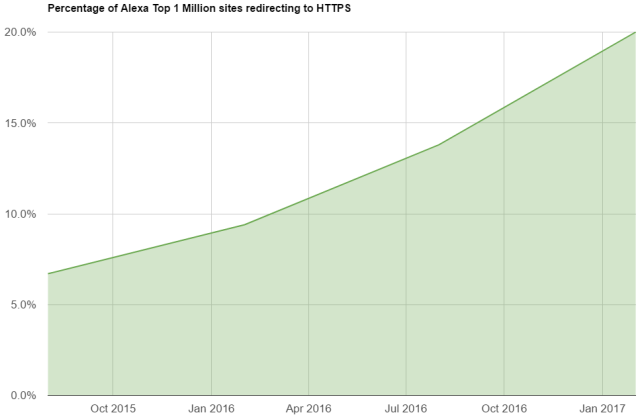
Percentage of top one million sites on HTTPS. (credit: Scott Helme)
Not only are we continuing to deploy HTTPS, the rate at which we’re doing so is increasing, too. This is what real progress looks like. The process of obtaining a certificate has become more and more simple over time and now, thanks to the amazing Let’s Encrypt, it’s also free to get them. Put simply, we send a Certificate Signing Request (CSR) to the Certificate Authority (CA) and the CA will challenge us to prove our ownership of the domain. This is usually done by setting a DNS TXT record or hosting a challenge code somewhere on a random path on our domain. Once this challenge has been satisfied the CA it issues the certificate and we can then present it to visitors’ browsers and get the green padlock and “HTTPS” in the address bar.