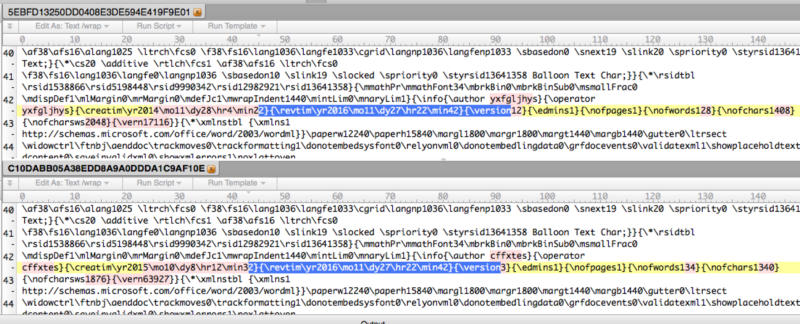
Enlarge / An identical artifact in two exploits, one installing Finspy and the other Latenbot. (credit: FireEye)
A critical Microsoft Word zero-day that was actively exploited for months connected two strange bedfellows, including government-sponsored hackers spying on Russian targets and financially motivated crooks pushing crimeware.
That assessment, made Wednesday with “moderate confidence” from researchers at security firm FireEye, is all the more intriguing because the payload delivered to the Russian targets was developed by Gamma Group, the controversial UK-based seller of so-called “lawful intercept” spyware to governments around the world. The company suffered a major setback in 2014 when a hack of its servers exposed more than 40 gigabytes of highly proprietary data showing that its software was used to spy on computers in the United States, Germany, Russia, Iran, and Bahrain. Gamma Group has continued to operate since then, as evidenced by Wednesday’s report showing that its software, known as Finspy, was installed as early as January using what until Tuesday was the zero-day vulnerability in Word.
Adding even more intrigue, the Word exploit used to install Finspy on Russian computers shares some of the same digital fingerprints as an exploit used in March to install crimeware. Known as Latenbot, the malware boasted a variety of capabilities, including credential theft, hard drive and data wiping, security software disabling, and remote desktop functions. The shared artifacts found by FireEye—which are documented in the image at the top of this post—strongly suggest the exploits used by both government spies and criminal hackers originated with the same source. That finding draws a connection between state-sponsored hacking and financially motivated online crime.