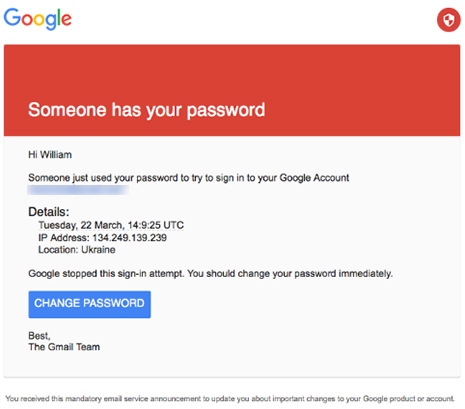
The spear-phishing e-mail received by Clinton campaign staffer William Rinehart matches messages received by both former Secretary of State Colin Powell and Clinton campaign chairman John Podesta. (credit: The Smoking Gun)
The breach of personal e-mail accounts for Clinton presidential campaign chairman John Podesta and former Secretary of State Colin Powell have now been tied more closely to other breaches involving e-mail accounts for Democratic party political organizations. Podesta and Powell were both the victims of the same form of spear-phishing attack that affected individuals whose data was shared through the “hacktivist” sites of Guccifer 2.0 and DCLeaks.
As Ars reported in July, the spear-phishing attack used custom-coded Bit.ly shortened URLs containing the e-mail addresses of their victims. The URLs appeared in e-mails disguised to look like warnings from Google about the victims’ accounts. These spear-phishing attacks were tracked by the security firm SecureWorks as part of the firm’s tracking of the “Fancy Bear” threat group (also known as APT28), a hacking operation previously tied to a phishing campaign against military and diplomatic targets known as Operation Pawn Storm.
As The Smoking Gun reported in August, one of these e-mails was sent to William Rinehart, a staffer with the Clinton presidential campaign. Rinehart’s e-mails were leaked on the DCLeaks site. DCLeaks also carried the e-mails of Sarah Hamilton, an employee of a public relations firm that has done work for the Clinton campaign and for the DNC. Hamilton’s e-mails were offered to The Smoking Gun by someone claiming to be Guccifer 2.0 via a password-protected link on the DC Leaks site.