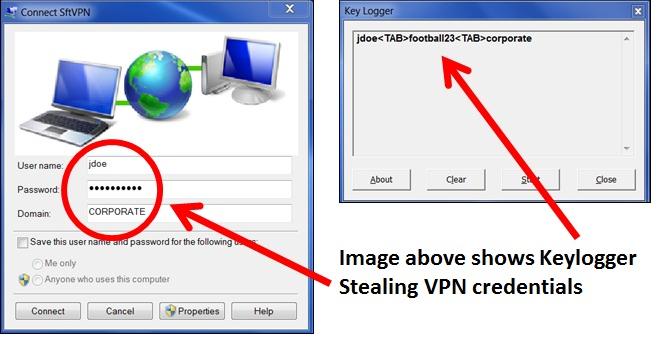
Enlarge / Keyloggers like this one surreptitiously store passwords and other confidential data entered into a computer. (credit: infosectoday.com)
HP is selling more than two dozen models of laptops and tablets that covertly monitor every keystroke a user makes, security researchers warned Thursday. The devices then store the key presses in an unencrypted file on the hard drive.
The keylogger is included in a device driver developed by Conexant, a manufacturer of audio chips that are included in the vulnerable HP devices. That’s according to an advisory published by modzero, a Switzerland-based security consulting firm. One of the device driver components is MicTray64.exe, an executable file that allows the driver to respond when a user presses special keys. It turns out that the file sends all keystrokes to a debugging interface or writes them to a log file available on the computer’s C drive.
“This type of debugging turns the audio driver effectively into keylogging spyware,” modzero researchers wrote. “On the basis of meta-information of the files, this keylogger has already existed on HP computers since at least Christmas 2015.”