Enlarge (credit: Palo Alto Networks)
It’s a mystery that left researchers scratching their heads: 132 Android apps in the official Google Play market attempted to infect users with… Windows malware.
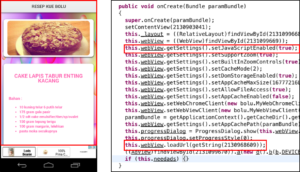
The apps, which were spawned by seven different developers, mostly contained carefully concealed HTML-based iframe tags that connected to two heavily obfuscated malicious domains. In one case, an app didn’t use iframes but instead used Microsoft’s Visual Basic language to inject an entire obfuscated Windows executable into the HTML. The apps were equipped with two capabilities. One was to load interstitial ads, and the other was to load the main app. The main apps loaded WebView components that were configured to allow loaded JavaScript code to access the app’s native functionality.
That was a lot of work considering that the Windows-based malware was incapable of executing on an Android device. On top of that, the two malicious domains in the iframes—brenz.pl and chura.pl—were taken over by Polish security authorities in 2013. So what, precisely, was going on?