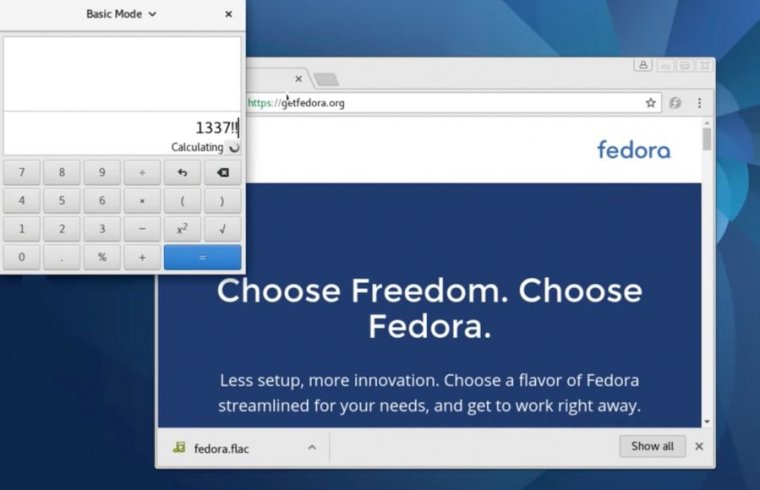
If you run a mainstream distribution of Linux on a desktop computer, there’s a good chance security researcher Chris Evans can hijack it when you do nothing more than open or even browse a specially crafted music file. And in the event you’re running Chrome on the just-released Fedora 25, his code-execution attack works as a classic drive-by.
The zero-day exploits, which Evans published on Tuesday, are the latest to challenge the popular conceit that Linux, at least in its desktop form, is more immune to the types of attacks that have felled Windows computers for more than a decade and have increasingly snared Macs in recent years.
While Evans’ attacks won’t work on most Linux servers, they will reliably compromise most desktop versions of Linux, which employees at Google, Facebook, and other security conscious companies often use in an attempt to avoid the pitfalls of Windows and Mac OS X. Three weeks ago, Evans released a separate Linux zero-day that had similarly dire consequences.