Audio, Not Video Over The LKV373 HDMI Extender
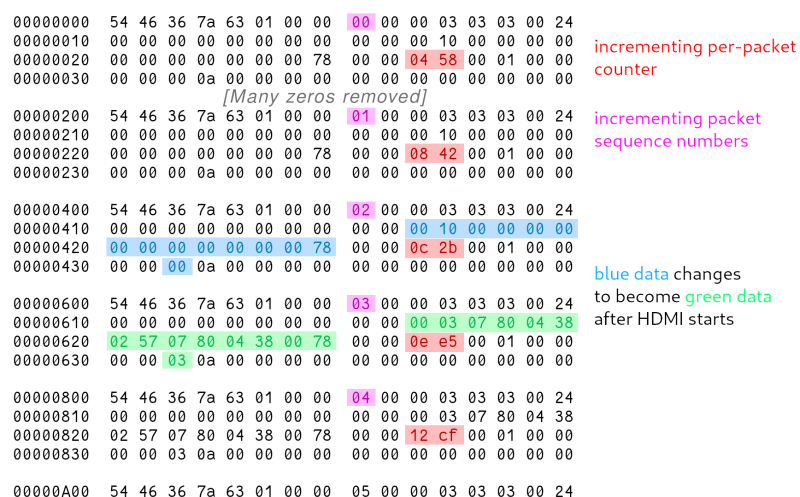
[eta] found herself in a flat with several LKV373 HDMI extenders. Find the corresponding transmitter, plug it into your device, and you’ve got a connection to the TV/sound system, no …read more Continue reading Audio, Not Video Over The LKV373 HDMI Extender
